Top 10 Identity and Access Management platforms
August 04, 2025 | Editor: Michael Stromann
17
Identity Management, Single Sign-On (SSO), Privileged Access Management (PAM), Customer identity and access management (CIAM) and 2-factor authentication (2FA) software.
1
Support enterprise-wide identity management across any app, user or device with Okta - a future-proof cloud service designed for maximum ROI & ease of use. A secure, reliable cloud service for today’s hybrid IT reality. Comprehensive Identity Management that has no alternatives. Across All Apps, Users and Devices. Easy-to-use, Superior ROI. Integrated, Future Proof
2
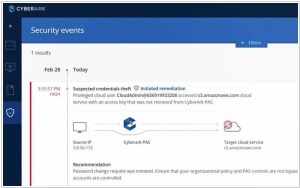
CyberArk is the only security software company focused on eliminating cyber threats using insider privileges to attack the heart of the enterprise.
4
Delivered as a cloud service with no hardware or software to deploy, IdentityNow provides fully-integrated IAM for compliance, provisioning and access management. IdentityNow meets the most stringent IAM-as-a-service (IDaaS) requirements and provides enterprise-grade services that meet security, scalability, performance, and availability demands.
5
Auth0 is the first identity management platform for application builders, and the only identity solution needed for custom-built applications.
6
Ping Identity offers secure single sign-on for your employees from any device and gives IT one dashboard to manage user access for all applications. Provisioning is available for popular apps such as Salesforce.com, Dropbox, Concur, WebEx, Box, Office 365 and more.
7
Learn why businesses and governments trust ForgeRock identity and access management solutions for everything from CIAM to IoT. Protect, connect, and manage the digital identities of people, devices, and the internet of things (IoT). We help large organizations secure the identity of anything, build trusted, personalized relationships with their customers, and provide a seamless omnichannel experience.
8
OneLogin provides the fastest path to identity management in the cloud with an on-demand solution consisting of single sign-on, multi-factor authentication, directory integration, user provisioning and a catalog with thousands of pre-integrated applications.
9
Keycloak is an open source identity and access management solution for modern Applications and Services. Add authentication to applications and secure services with minimum fuss.
10
Amazon Cognito lets you add user sign-up, sign-in, and access control to your web and mobile apps quickly and easily.
11
Cloud Directory Platform. Securely manage identities, access, and Windows, macOS, & Linux devices from anywhere, using a single platform, with unified user identities across IT resources.
12
Quest One Identity is a cloud-based access and identity management solution that simplifies complex and repetitive tasks — so you can focus on driving your business forward.
13
BeyondTrust PAM products empower you to protect identities, stop threats, and deliver dynamic access to enable and secure a work-from-anywhere world. Watch a demo today!
14
Identity tools from Google help you quickly build an auth system that will grow with your business and reduce the friction of getting users into your app.
15
Cloud-ready, enterprise-grade PAM solutions that put privileged access at the center of cybersecurity strategies
16
European Leader In Privileged Access Management. Easy to use and easy to deploy, the WALLIX Bastion PAM solution delivers robust security and oversight over privileged access to critical IT infrastructure. Reduce the attack surface and meet regulatory compliance requirements with simplified Privileged Access Management.
17
Two-factor authentication done right. Duo Security lets your users use their mobile phones to secure their logins, protecting your company from account takeover. Duo’s solution is cloud-based, which means there's no software to install, and no server to set up. Our patented technology and drop-in integrations enable you to seamlessly integrate Duo into your existing application login workflow. Owned by Cisco.
18
SecureAuth provides a single platform to enable access from any glass to any app, serving over 500 customers worldwide.
19
BetterCloud secures user interactions across your digital workplace. SaaS Management and Security that is customized to your business.
20
Centralize authentication and authorization services to ensure only authorized users gain access to resources.
21
Microsoft Entra allows to secure access for a connected world, protect any identity and secure access to any resource with a family of multicloud identity and network access solutions.
Important news about Identity and Access Management platforms
2025. Palo Alto Networks acquires secure identity platform CyberArk for $25B

Cybersecurity giant Palo Alto Networks is buying identity management and protection company CyberArk. The deal is one of the biggest in the history of the IT market - $25 billion. And, naturally, this is the largest acquisition for Palo Alto Networks, which previously bought Dig Security ($400 million in October 2023), Talon Cyber Security ($625 million in November 2023) and Bridgecrew ($156 million in February 2021), among others. Palo Alto CEO Nikesh Arora says that with this acquisition, the company enters the identity security market and gets a platform that can solve the looming problem of AI agents that learn to authenticate instead of people.
2025. Identity Management platform CyberArk acquired Zilla Security

Identity security company CyberArk has acquired identity governance and administration (IGA) platform Zilla Security in a deal worth up to $175 million. CyberArk specializes in access management, including privileged access security which helps organizations protect sensitive data and critical infrastructure from external (and internal) threats. Zilla is a nimbler cloud-native player that has been adding more automation and AI-enabled features to the mix, making it an alluring proposition for a much larger company founded in the days before SaaS or cloud computing had taken hold. Thus, CyberArk hopes to "reshape identity governance with scalable automation that delivers compliance and helps maximize security for the modern enterprise".
2023. Google Authenticator can now sync 2FA codes to the cloud
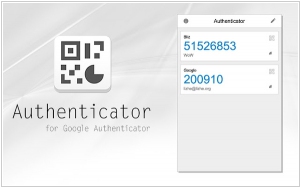
Google Authenticator has been updated to enhance its usability for those who frequently utilize the service to log in to websites and apps. Starting today, Google Authenticator will synchronize any one-time two-factor authentication codes that it generates to users' Google Accounts. Prior to this update, these one-time codes were saved locally on a single device. As a result, losing the device meant losing access to any service set up with Authenticator's 2FA. By updating the Authenticator app, users can take advantage of the new synchronization feature. If they are signed in to a Google Account within the Authenticator app, their codes will be automatically saved and restored on any new device they use.